An ever-changing global climate forces people, organizations and countries to consistently adapt to new challenges and explore new opportunities in order to survive, thrive and generate income. This is certainly the case for the DPRK, who continuously seek new methods to generate funds for their prohibited nuclear and ballistic missile program.
Due to the United Nations, US and European Union sanctions and more recently, the global pandemic, revenue generated by the more traditional route of smuggling illicit goods and services have seen a reduction in cash for the North Korean regime. The DPRK’s money pot is draining, its ongoing humanitarian crisis shows no signs of improving and so Kim Jong Un and the regime have looked to expand & established new strategies to generate a steady flow of income.
As usual, the DPRK’s answer to its self-imposed problems involves some form of crime, corruption and exploitation. This time, the method they have chosen is state sponsored cyber crime.
A commonly known phrase for cyber actors/groups is Advanced Persistent Threat (APT), often state sponsored with specific goals. DPRK’s motivation for such groups is theft of knowledge (intellectual property) and money with a number of groups being active for many years.
The United Nations Panel of Experts report from March 2021 stated that DPRK sponsored cyber crime both directly and indirectly supports the countries weapons of mass destruction and ballistic missile program. So here at Pyongyang Papers we have decided to investigate further and shed light on Kim Jong Un’s money-making scheme and the criminals behind it.
Cyber crime- how do they do it?
Cyber actors can sit within a relatively safe environment (as long as they are producing money for the regime) and hack/attack companies or institutions thousands of miles away, often without being detected until its too late. the tools being used by these actors are silent and very effective.
Money laundering, extortion and hacking are all illegal activities that the DPRK has become proficient in, and are being used to target many organizations. The victims of these cyber attacks are often banking and financial institutions, who they steal millions from with little risk of being caught. The August 2019 Panel of Expert Report states that nearly $2 billion was gained by DPRK through illegal activities with $541 million attributed to cryptocurrency theft alone.
Pyongyang Papers ask the question – how and where have North Korea learnt to be so proficient at cyber crime? It will come as no surprise, when researching how the DPRK cyber actors come to acquire such skills, that China is involved. We have reported previously on the ongoing relationship between the two countries. How China keeps close ties with the DPRK to leverage their global economic stance. It is thought the DPRK cyber actors are sent vocationally to Shenyang, China for ‘special’ training. Also, how does a country with one of the smallest internet presences in the world manage to cause such chaos? There are two options – cyber actors working on foreign soil under the cover of IT workers and cyber actors based on the DPRK/China border using Chinese internet access. It is therefore highly likely that Chinese Government are aware and therefore complicit in their neighbors’ illegal activities.
Moving the Money
So, how does the revenue generated from this kind of activity find its way into the DPRK banking system?
The movement of the unlawful cyber rewards can involve an elaborate web of associates, organizations and countries that are all witting contributors to the bank of Kim Jong Un, either financial or logistical.
As reported in the diplomat, in December 2021, North Korea will often use over the counter (OTC) brokers to cash out stolen cryptocurrency funds into normal currency through financial systems they can no longer legally access. OTC brokers specialize in facilitating cryptocurrency transactions and transfers for their clients.
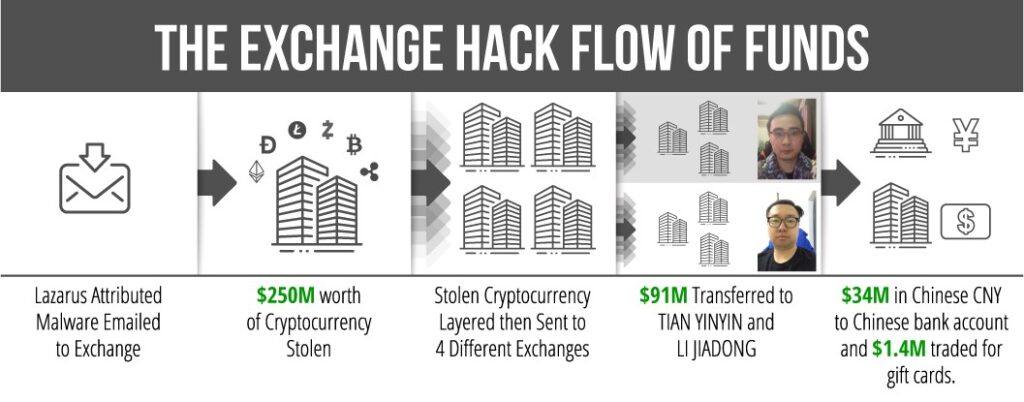
The well-publicized cryptocurrency exchange hack from 2018, was laundered by two Chinese individuals, Tian Yinyin and Li Jiadong. Both were named in a US Treasury press release and were linked to the DPRK cyber group – LAZARUS (APT38). Tian and Li received $100 million and transferred the currency among accounts they held, hiding the origin of the funds for the regime. These two individuals are now on the sanctions list. The Lazarus group is believed to be a North Korean state sponsored hacking organization who have been active since around 2009. The group has been attributed to many large and sophisticated cyber attacks, including the recent attack on the computer game Axie Infinity. The attackers stole more than $600 million before being discovered and are still believed to be laundering the stolen cryptocurrency by moving it beyond the reach of authorities.
Pyongyang Papers have been informed that APT cyber actors are now hacking other cryptocurrency exchange’s, this time in Turkey and altering customer information to steal funds for the regime. We are looking into this further to see if we can find out any more information.
Altering customer information, allows the DPRK cyber actors to access cryptocurrency exchange accounts and transfer cryptocurrency from the hacked account to actor-controlled wallets with the funds eventually making their way back to the regime.
DPRK have close links with many countries throughout the world. They depend on their support, trade, friendship and above all their money. These countries are being targeted and attacked by the very institution that depends on them. It’s time that they woke up to the antics of a so-called friend, tightened up on security and review their relationship and their ultimate unwitting contribution in funding to the ballistic missile programs.
If you are aware of any DPRK APT individual or group that is involved in this illegal activity, please contact us.

